Islamabad: The Kaspersky Digital Footprint Intelligence team has uncovered nearly 40,000 dark web posts about the sale of internal company information over the past two years. These posts – created by cyber criminals – are used to buy, sell or distribute data stolen from various companies through cyber attacks. The number of places offering access to enterprise infrastructure saw an increase of 16% compared to the previous year. Globally, one in three companies has been mentioned in dark web posts related to data sales or access.
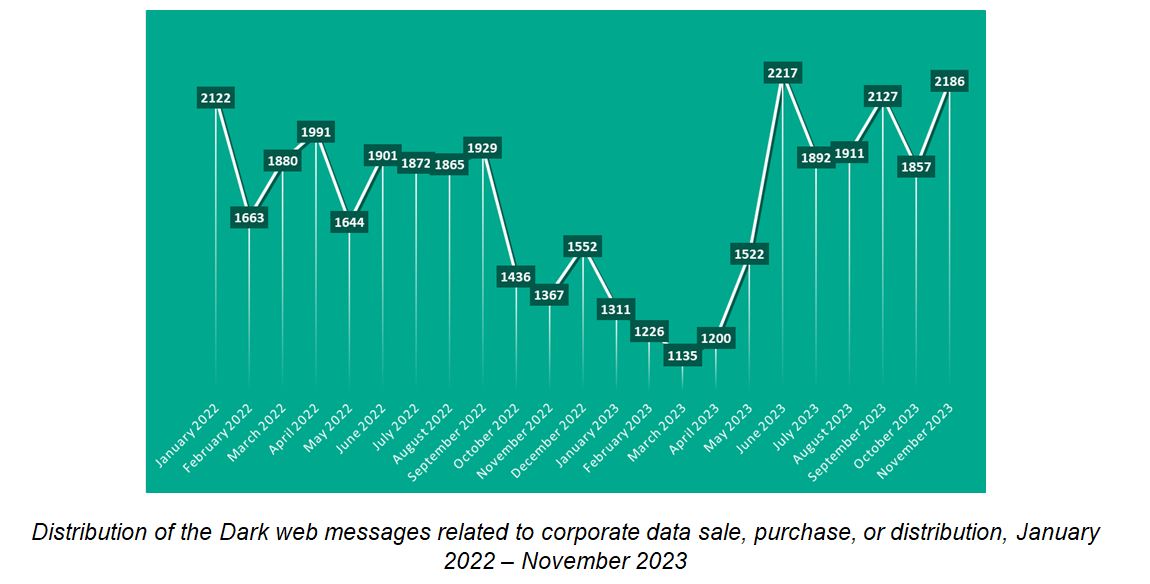
Kaspersky Digital Footprint Intelligence experts observed an average of 1,731 dark web messages per month about the sale, purchase, and distribution of internal corporate databases and documents, for a total of nearly 40,000 messages between January 2022 and November 2023. The monitored sources included dark web forums, blogs, and also shadow telegram channels.
Distribution of dark web reports related to the sale, purchase or distribution of corporate data, January 2022 – November 2023
Another category of data available on the dark web is access to corporate infrastructure, allowing cybercriminals to purchase pre-existing access to a company, allowing attackers to streamline their efforts. According to Kaspersky research, more than 6,000 dark web messages advertised such offers between January 2022 and November 2023. Cybercriminals are now increasingly offering access, with the average number of corresponding monthly reports witnessing a 16% increase from 246 in 2022 to 286 in 2023. While the number of reports may not seem high, it does not diminish the potential severity of the problem. With the looming threat of supply chain attacks in the coming year, even breaches targeting smaller companies could escalate to affect many individuals and businesses around the world.
“Not every message on the dark web contains new and unique information. Some offers may be repeated; for example, when a malicious player is trying to sell data quickly, they can post it on various underground forums to reach a larger audience of potential criminal buyers. In addition, some databases can be combined and presented as new. For example, there are ‘combolists’ – databases that collect information from various previously leaked databases, such as passwords for a specific email address,” explains Anna Pavlovskaya, an expert at Kaspersky Digital Footprint Intelligence.
To further enhance the security of businesses worldwide, Kaspersky Digital Footprint Intelligence experts tracked mentions of 700 random companies related to corporate data compromises in 2022 and provided information on cyber threats originating from the dark web.
The findings revealed that 233 organizations – one in three companies – were mentioned in posts on the dark web related to illegal data sharing. These links specifically included topics such as data breaches, stolen access to infrastructure, or compromised accounts.
Additional statistics on dark web discussions are provided on Securelist, while the Kaspersky Digital Footprint Intelligence website provides a comprehensive incident response guide for dealing with incidents related to the leak. In order to avoid threats related to data breaches, it is worth implementing the following security, including rapid identification and response to data breaches is essential. Essentially, the company needs to gather evidence to confirm that an attack has occurred and that data has been compromised. Continuous monitoring of the dark web allows detection of both fake and genuine breach-related posts, as well as monitoring increases in malicious activity. Because monitoring the dark web is resource-intensive, external experts often take over this responsibility.
40,000 dark web posts about corporate data surfaced in past two years: Kaspersky Report